Cybersecurity
Cybersecurity Strategies Critical To Production Operations
By Peter Zornio and Michael Lester
AUSTIN, TX.–Recent advances in digital automation technologies such as cloud-based data analytics, wireless instrumentation, industrial networking and machine learning have opened a world of opportunities hardly imaginable even a decade ago. These new tools and the advent of the Industrial Internet of Things (IIoT) have enabled remarkable improvements in efficiency and reliability, but they haven’t come without costs.
Chief among these, and ultimately owned by digital oil field operators, is the issue of cybersecurity risk. At a time when headlines about industrial terrorism, ransomware and corporate espionage are the new norm, it is clear that oil and gas companies must change their collective culture to solidify a close relationship between their information technology and operational technology functions, and work with automation suppliers and regulators to respond to today’s quickly-changing security landscape.
The upstream sector faces a unique set of challenges because of the complex nature of the production process, the associated safety issues and environmental hazards, and physically remote assets. IIoT-based technologies have made it possible to solve many of these problems, leading an increasing number of operators to look at digital transformation as a strategy for increasing bottom-line profitability.
Digital oil fields are a prime example of this approach. Digital oil fields leverage near real-time production data from wireless instrumentation transmitted from wells in the field across secure networks to cloud-based reservoir modeling software that continuously updates. Digital workflows automate seismic interpretation and depth conversion to provide a clearer understanding of the reservoir’s geology and make it possible to optimize future drilling campaigns and operations.
Equipment miles out in the field is monitored by centralized predictive diagnostic software that analyzes flow rates, valve positions, vibration levels, tank levels and more, to identify problems before they impact production. Engineers and technicians can connect to and troubleshoot systems remotely, reducing maintenance costs and minimizing man-hours spent in the field. Nevertheless, for all the advantages these kind of data-driven operations create, the fact remains that they also can expose operators to an array of security threats that are constantly evolving and becoming ever-more difficult to prevent or stop.
Attack Vectors
Well pads, drilling rigs, pipelines, platforms, terminals, tanks–some of which can be hundreds of miles from the nearest control room–are all vulnerable to attacks that are increasing both in number and complexity. New technology implemented correctly with cybersecurity controls can bring value to the digitally transformed oil field. Implemented incorrectly, a trespasser with a pair of bolt cutters and a laptop, for example, potentially could gain access to a programmable logic controller on an air compressor via Bluetooth, order a PLC to exceed operating parameters and discontinue operations. Standard security measures may be in place, but turning measures into procedures is difficult and passwords can be stolen. The reality is that as soon as one oil field network is connected to other networks, the chance of attack increases exponentially, especially if connected to open networks or the Internet.
Obviously, the worst-case scenario is any threat that compromises people’s safety or the environment, including acts of terrorism and vandalism. For example, a denial-of-service attack launched over the Internet to disable hydrogen sulfide detectors on an offshore platform could expose crews to toxic gases or disrupt communications to a transfer system and cause a spill. Other scenarios, such as stolen credentials used to remotely access and shut down drilling rigs or pumpjacks, could cause millions of dollars in losses.
One of the most common motivations for targeting a digitized oil and gas operation is to steal commercially sensitive information, such as well output data, which could benefit competitors or affect stock value, if publicized. Simple vandalism is as big of an issue as politically motivated nation-state attacks or terroristic threats by nongovernment actors. Whatever the motivation, the diversity and sophistication of threats has expanded enough in only the past five years to warrant a fundamental reassessment of how well the industry protects itself.
While a single successful attack may have a limited immediate financial impact on an organization, multiple attacks over time can begin to inflict significant collateral damage by heightening uncertainty about the setting of the next attack, and how well industry standards are performing against the growing sophistication of viruses, malware and other cyberthreats. In this way, a series of smaller attacks may have a magnified effect by potentially undermining the market’s confidence in the security of the world’s energy infrastructure.
Protection Strategies
With stakes so high, the fundamental question asks what digital oil field operations are doing to protect themselves against cyberattacks, and if that is enough. Let’s examine a few key characteristics and shortcomings of a typical digital oil field.
One obvious solution is to physically isolate certain assets by “air-gapping,” or completely disconnecting equipment from any networks. While this provides the maximum level of protection possible, it severely limits opportunities to optimize production in revenue-increasing ways. Properly analyzing the cost of air-gapping versus its security benefit is key. Most extensively connected oil field networks rely on network equipment with different levels of technical capabilities to secure connected devices and assets. A network is only as secure as its weakest link, and many legacy systems in use today are not sophisticated enough to adequately manage complex traffic, access and command structures with a defense-in-depth strategy.
Organizational factors also can affect digital oil field networks’ security, including disparate cybersecurity teams responsible for different aspects of the operation. If a network can be thought of as pipelines of data that need to be instrumented, analyzed and controlled, it is essential from an operational standpoint to know what data are going where and how to direct data flows to help refine work methods and improve decision making while maintaining appropriate cybersecurity controls. Many companies rely on cybersecurity programs that cover only part of their operations; their assets and networks typically are not monitored end-to-end by a centralized team working on a 24/7 basis.
Some businesses elect to hire third-party experts to assess their vulnerabilities and defense measures, and recommend procedures. Security consultants examine operators’ answers to questionnaires and evaluate technologies and workflows against standards such as the IEC 62443 series. This can provide a base line to demonstrate what a company is and is not doing sufficiently well. For perceived cost reasons, some companies elect to handle these duties using in-house personnel who often have limited training in risk assessment and problem solving, or elect to use corporate-level experts unfamiliar with individual facilities or security practices, such as procedures for handling USB or thumb drives in an operational environment.
Pragmatic Approach
Digital transformation is a multifaceted process; some businesses undergo it gradually, incorporating new technologies as they gain confidence in their reliability and investment value. The key is to keep pace with the threat’s evolving nature, adapt to changes, and remain flexible from an organizational and technological standpoint. This requires a pragmatic approach that emphasizes developing and incorporating new tactics and insights gained from failures.
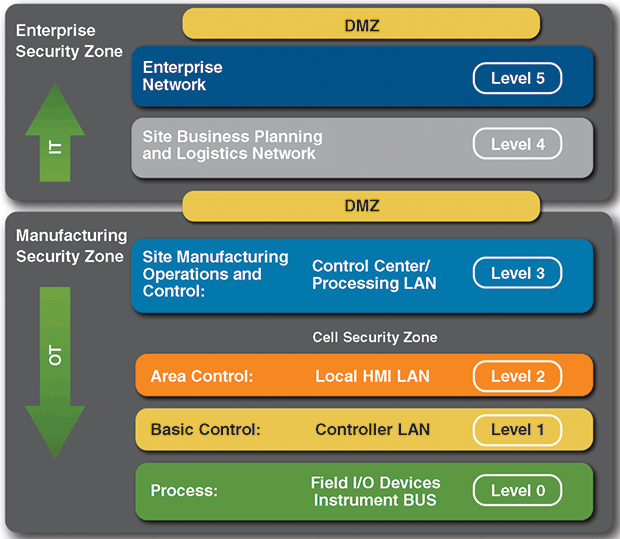
FIGURE 1
Network Segmentation of Business
And Industrial Control System Architectures
Source: U.S. Department of Homeland Security’s National Cybersecurity & Communications Integration Center and Industrial Control Systems Cyber Emergency Response Team
The first consideration is for operators to focus on their business objectives, connecting only what will help achieve business objectives. Their plans should start small and scale up to maintain the right balance between connectivity and security by properly partitioning networks into physical segments, and adding additional security controls where needed (Figure 1). Using virtual local area networks (VLANs) for segmentation should not be considered secure, since they are prone to VLAN-hopping, which is a network attack vector commonly used to gain access to systems on VLANs not in the route scope of the originating VLAN.
Using VLANS also can enable a technique called pivoting on a system with access to multiple VLANS to gain access beyond intended authorization. This method can be used to steal credentials, install malware or perform other malicious activities. Upgrading network firewalls from network layer three to network layer seven protection vastly improves administrators’ ability to manage traffic, control access and limit or block command functions and privileged use.
Data security is always a critical issue in digital workflows. Data availability in a digital oil field operation is essential to achieving performance improvements, but its importance raises the problem of how to structure an enterprise system to ensure information is stored and distributed safely. Historically, a common approach is based on multilayered reference architecture models for securing digitized oil fields. While these models are evolving to meet new technology and connection methods, they are rooted in the Purdue Reference Architecture, which is extrapolated in IEC 62443-3-3 Appendix A to “zones” and “conduits” using a five-level approach. Modifications include adding a sixth “external” level in the enterprise zone:
- Level 0: The physical process of drilling, producing and operating fields;
- Level 1: Intelligent devices such as wireless sensors, analyzers, actuators and related instrumentation;
- Level 2: Control systems such as human-machine interfaces, and supervisory and data acquisition software;
- Level 3: Operational systems, including reservoir modeling, predictive diagnostics, data historians and related middleware;
- Level 4: Business logistics systems to manage the business-related activities of the operation; and
- Level 5: External, including private, public and hybrid cloud or hosted services and infrastructure.
By configuring security zones and conduits based on this reference architecture as specified in the IEC 62443 standard, upstream operations can provide a sound, supportable level of secure architecture that supports their operations based on industry collaboration and guidance. As a rule, however, there always should be an identifiable business reason–whether it is to improve safety or productivity–for connecting any given asset. Convenience never should be the driving force behind any digital transformation strategy.
Intrusion detection systems alert administrators when unauthorized connections are attempted or made, but they only identify attacks; they don’t stop them. Intrusion prevention systems (IPS) actually can block connections according to preconfigured policies and definitions. Subscription services can be employed to update malicious connection information and identify malware and command and control servers. IPS subscriptions provide the benefit of blocking known malicious connections based on shared industry and global cybersecurity intelligence.
Other Considerations
Other fundamental considerations for ensuring safe and secure digital oil field operations include:
- Leveraging behavioral analysis;
- Performing system audits and assessments;
- Carefully selecting equipment and service vendors;
- Properly training personnel on both technology and procedures; and
- Using key performance indicators to benchmark cybersecurity performance.
Behavioral analysis techniques include polices and workflows designed to flag abnormal behavior in both personnel and systems. A combination of controls–such as a security incident and event manager that aggregates logs from security and other systems, along with an intrusion or prevention detection system–put both electronic detection policies and operational cyber-response capabilities in place to speed the detection of abnormal behavior and give security teams more time to detect and neutralize an attack. Deploying carefully designed electronic and physical workflow authorization procedures can help to protect critical processes as well as implement change management strategies across organizations.
Instituting regular audits and assessments to identify security gaps is an essential component of any successful strategy, but it is also important to review the assessment process itself periodically to determine its effectiveness in finding and addressing threats. This may involve auditing systems to achieve the appropriate security posture based on the risk tolerance determined in the risk assessment process, which if thorough, will identify gaps either in the technology apparatus or the implementation of policies and procedures.
Many digital oil field operators engage some level of outside expertise to maintain, run and optimize their systems, as well as devise and execute cybersecurity strategies. Based on the results of security assessments, a company may have to engage an expert to address a complex vulnerability. In this case, it is critical to hire experts with experience and a level of familiarity relative to the operations, systems and devices being protected. With so many variations in how to implement and sustain security objectives, it is important to choose experienced technology vendors that specialize in enhancing both security and productivity across a customer’s entire organization.
With regard to training, as with safety, cybersecurity should be everyone’s responsibility. It has many domains of expertise that require continuous training to maintain the knowledge and skills necessary to run a modern, digitized oil and gas operation. Implementing technology that can affect technical controls or processes adversely is easy to do without adequate workforce competency development strategies. Training personnel on processes and procedures that both identify the types of technology and procedures to follow are key to reducing risk. All levels of the organization should require training that emphasizes security processes and technology. Instilling cybersecurity measures as part of a company’s culture requires various levels of training, from simple awareness campaigns to expert-level instruction.
Finally, determining how to best benchmark cybersecurity performance requires a deep understanding of the business objectives, risk tolerance, policies and capabilities. These concerns can be challenging to integrate into an effective reporting system, but establishing the right KPIs must happen at various levels. While executive and board-level KPIs are more a measurement of organizational maturity, operational KPIs are better indicators of how well security tools are being implemented.
As an example, if a company is told there are 10,000 vulnerabilities across 100,000 systems (the number of vulnerabilities is a typical cybersecurity measurement), it may mean little at the board level because of the technical knowledge required to interpret the actual risk. It probably will resonate more effectively if, instead, the board is informed that 98 percent of identified vulnerabilities have been patched during the past month without operational disruptions, and that the cybersecurity risk to business operations from active known attacks has been reduced. The key is to choose meaningful measures that lead to taking the right cybersecurity posture necessary to meet a company’s given business objectives.
Working In Concert
Automation suppliers are partnering with oil and gas producers to better safeguard their customers’ products and systems using these types of best practices while also developing new ones that leverage the right technology for the right purpose. This includes strategies such as faster software patch rotations, which can make it easier to maintain patches and configuration changes with regularity to meet direct and indirect threats. Some suppliers make security patch management available through product life cycle services, as well as internal processes enabled by new secure connectivity models and product capabilities that can reduce outages.
Some process control systems not only can detect, but also prevent, attacks using methods such as “whitelisting,” where only predetermined programs are authorized to run. Such methods increasingly are being incorporated into field devices and systems used in upstream applications beyond the control room to detect malicious activities and provide valuable data to security personnel through standard product features.
As mentioned, data availability is a critical factor when it comes to performance, but it also is an area where IIoT-based innovations can be leveraged to make operations safer. Oil field networks and systems are much like a process control loop: If networks and systems are not instrumented for cybersecurity operations, the operator cannot know what actually is happening within them. Digitizing workflows and ensuring that the right data get to the right personnel allows operators to concentrate on making better operational decisions that not only guard sensitive systems and assets against attacks but increase performance.
An example of integrating data systems for enabling both improved decisions and enhanced operational security is an automated solution that uses pervasive sensing and machine learning technology to tightly integrate static and dynamic data domains and provide near real-time insight into the efficiency of exploration, drilling, completion and production activities. Automation suppliers also are developing new secure architectures that enable access to so-called stranded data and provide appropriate security levels in legacy environments using modern technology such as data diodes, digital twins, private cellular networks and application-level fire walls.
In a world where the question operators must ask is not whether they will get attacked, but rather when (and how will it impact the bottom line), it is important to maintain a business-risk perspective when it comes to the role of cybersecurity in the digital revolution, now and into the future. Oil and gas companies have an increasingly diverse set of tools at their disposal, but they must remain vigilant–even paranoid–about protecting their assets.
People, processes and technology must work in concert to achieve the right balance of risk and business performance, both online and off.

PETER ZORNIO is chief technology officer at Emerson Automation Solutions. He is responsible for the strategy and implementation of Emerson’s technology programs, portfolio direction and standards across the group. He joined the company in 2006 after serving 11 years at Honeywell in advanced applications, product and industry marketing, and technology roles. Zornio is a member of the Forbes Technology Council and holds a B.S. in chemical engineering from the University of New Hampshire.

MICHAEL LESTER is director of cybersecurity strategy, governance and architecture at Emerson Automation Solutions, where he oversees the global implementation of cybersecurity solutions in the company’s products and services. He joined Emerson in 2007 after serving 22 years in the U.S. Air Force, with the final 10 years specializing in information technology and network security, information systems management and business intelligence. Lester holds associate degrees in information systems technology and aviation maintenance technology from the Community College of the Air Force, and a B.S. in management/information systems from Park University.
For other great articles about exploration, drilling, completions and production, subscribe to The American Oil & Gas Reporter and bookmark www.aogr.com.