Trends Reflect Evolving Industry Needs, Challenges
By Neale Johnson and Hemme Battjes
NEW YORK–Energy companies will face significant changes over the next 20-30 years, ranging from greater demand for different types of energy sources–and subsequent competition–to continued mega mergers and the associated consolidation of services and reduction in costs.
As these changes take place, there will be ongoing investment in new computing technologies. Companies already are accelerating investments in computing innovations beyond those of the early adopters as they see the business benefits of doing so. The key going forward will be to filter technology developments and target those that deliver the greatest value to a particular organization.
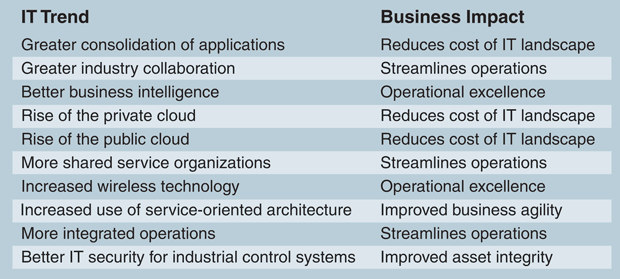
Table 1 shows 10 technology trends that Accenture believes hold significant potential to support energy companies as they evolve to a new energy era. Research within the chief information officer network points to four trends that consistently appear high on CIOs’ agendas: cloud computing, IT security, wireless networking, and analytics.
Cloud Computing
The past 10 years have witnessed the commoditization of hardware and operating systems. Most oil and gas companies try to minimize the complexity of their hardware and operating systems by establishing standard environments. The evolution of this standardization trend led to the more recent trend of “virtualizing” servers.
Hardware and operating system templates are moved into a virtual environment and IT infrastructure is completely separated from applications. Virtualization already is a well established and proven approach for many oil and gas companies. These companies are better positioned to streamline and manage their IT organizations by lowering costs, minimizing risks and increasing the agility of their IT infrastructures.
One supermajor has moved almost all the servers in its global data centers into VMware ESX environments, and 15,000 servers have been virtualized to date. This move sets the stage for further adoption of cloud services, both private and public clouds.
The private cloud, which is virtualizing hardware, centrally hosting standard applications and moving local systems to global data centers within the borders of the enterprise, offers many of the advantages of cloud computing, such as increased IT resource availability and lower costs. The private cloud also eliminates public cloud downsides such as security concerns and vendor lock-in, which means entire business functions could be in the scope of functions deployed to the private cloud.
The public cloud refers to subscribing to software-as-a-service (SAS) services from the Worldwide Web. No internal hosting is required, only Internet access. Security of information and physical assets is paramount for the oil industry, and when it comes to adopting SAS, IT management generally has concerns about accessing specific data, recoverability, and the level of reliability that can be achieved, among others.
This leads Accenture to believe that in the short term, SAS will be adopted in areas where security concerns do not inhibit deployment. Security concerns can be overcome for SAS areas where a strong track record for security and risk control can be found. These generally are noncore areas such as human resources or finance.
SAS also can be used for quick implementations. For example, a gas company in Asia-Pacific needed an asset management application during its design phase. Since time was a factor and implementing a typical asset management application takes some months, the company decided to subscribe to a computerized maintenance management system vendor’s SAS. By doing so, the company managed to get an asset management application up and running in weeks.
Longer-term opportunities for adopting SAS exist for supply chain management. However, within a supply chain, certain areas such as managing supplier relationships, global trade and supply chain events as well as transportation, already have started to show some movement toward SAS.
IT Security
IT security is critical to organizations for two key reasons: thwarting the wave of cyber attacks and obtaining a solid, secure infrastructure that can take advantage of technologies on the horizon. The inclusion of cyber security as a special session topic at the 20th World Petroleum Congress in December in Doha, Qatar, indicates the degree of attention companies are placing on securing information and control systems, and the safety of their infrastructure.
New levels of interconnectedness have made industrial IT, especially distributed control systems (DCS), more open and vulnerable than in the past. DCS and supervisory control and data acquisition systems no longer are fully isolated from outside networks, systems and users. As a result, energy companies must deploy security software, processes and governance more rapidly to secure their data and legacy process control systems, many of which were conceived in non-networked environments.
Often, one or some of these data or process control systems are connected to a public network such as the Internet. As an example, using a public network to maintain and optimize a plant on time and cost effectively exposes that plant to attackers. However, industrial control systems without Internet connections also are vulnerable, as was seen with the Stuxnet virus, which was spread through infected USB flash drives.
Stuxnet, which many experts believe is the most advanced malware ever built, was designed specifically to take DCS and SCADA systems with the purpose of damaging industrial systems. Systems that did not meet the specific configuration requirements were not attacked.
More recently, the Duqu virus was discovered last September. According to research by Symantec Corporation, Duqu was developed by the same people who authored Stuxnet. The purpose of Duqu was completely different, however. It was designed to target particular assets of specific organizations by gathering intelligence from units such as industrial control system manufacturers, to prepare to execute future attacks.
It is worth noting that older DCS and SCADA systems were not designed to support even basic security and safety features. Often, only physical access to a computer terminal or network cable is required to have full access to all parts of the system, thereby leaving them vulnerable to external manipulation. With the increasing complexity of control systems in industrial plants, the level of impact any external threat may have has grown correspondingly.
Users, too, have a critical role to play in security, as the case of a hacked Houston water treatment plant illustrates. The plant users had a three-letter password and didn’t change it. The combination of external hacking and lack of internal governance drives home the point that it isn’t only the tools; users have to be vigilant, too.
Security Vendors
The Stuxnet and Duqu worms have accelerated the trend of energy companies revalidating security in industrial IT and general IT infrastructure. This can include a wide range of safety measures such as restrictions on physical access, intrusion detection, sophisticated network segmentation with firewalls, etc.
Because of a shortage of IT skills inside their own organizations, many energy companies are turning to IT security vendors to provide customized solutions for specific plants. Some vendors have developed comprehensive security software packages, or “IT security in a box.” These packages attempt to fulfill security requirements for different situations using a certain security architecture that is available in an off-the-shelf software package.
Often, this is very expensive, especially for smaller sites. At larger sites, these software packages are often compromised when they are integrated with legacy systems. It should be noted however, that IT security requires more than hiring a service provider for advice on how to secure the business properly. It involves bringing in a team with the right mindset, security policies and procedures, investments, training of staff, and a corporate culture focused on security, to name a few.
Wireless Technology
The growth and ubiquity of safe, fast and reliable wireless communications can provide access to data in any part of the plant. Operators can interact in real time through all manners of mobile devices–from “traditional” notebooks to tablets and smart phones–to exchange voice, video, photos and data without needing to install expensive networking infrastructure.
Wireless Technology can add business value in several ways:
- Sensor devices that provide continuous, real-time monitoring capabilities can improve the quality and efficiency of natural gas and petrochemical processes.
- Increased input from RFID (radio frequency identification) tagging of assets and people improves business intelligence.
- Tracking and tracing technologies for mobile assets and employees increase control and reduce the amount of errors and accidents, thereby improving compliance.
A good example of using wireless technology can be seen in action at Marathon Petroleum Company. Marathon is using a wireless-enabled gas detection system that helps protect workers in potentially hazardous environments. The solution combines Wi-Fi and location-based technologies with gas detectors, which enable Marathon to monitor personnel remotely within the facility, as well as to detect any gas release incidents.
BI And Analytics
Information often is hidden in organizational silos in oil and gas organizations. Multiple systems hold multiple versions of the “truth,” and before information can be used in decision making, its quality should be ensured for both received and extracted data. This often requires significant information gathering and manual correction of underlying data. Business intelligence (BI) often is seen as the Holy Grail in connecting information flows with decision making.
BI is not a new trend. The term was popularized almost two decades ago, but adopting BI has not been as easy as many organizations had hoped. This has led to a continuous desire by IT managers to apply data management and extract valuable information, which has caused BI to be on the top of CIOs’ agendas for many years. A 2007 Accenture survey of CIOs in the United States and Europe found that more than 75 percent of respondents wanted to develop an overall information management strategy within the next three years.
Several developments will enable BI to truly add value. These include the shift from measuring historical data and presenting them in the form of dashboards or reports, to analytics and forecasting. This shift came about because of the availability of advanced analytical tools, and in part by the outsourcing of certain data services and management to specialists in order to address increasing skill shortages, and to realize economies of scale and manage costs.
BI increasingly is integrated with collaborative decision making. Often it even enables collaboration through easily accessible and automated reporting, immediate integration into business applications, and in some cases as a Web 2.0 solution.
Successful BI solutions are those that keep the business user in mind, go for the “low-hanging fruit,” and move companies forward in small steps, rather than trying to solve all problems at once. For example, an Eastern European oil and gas company started its BI initiative with operations reporting at only one refinery. Over time, the company centralized more sites and data sources to create a single reference for different types of data, such as shop floor, supply chain, finance, and health and safety.
These trends are driving energy companies to improve the way they operate in an ever-changing industry. As the technology landscape moves toward more flexible infrastructure, and more open systems and processes, industry CIOs are being required to become service integrators who must be more involved with internal business users and external stakeholders in order to keep pace with technology developments.
The result is that today’s IT services are a utility that, at a minimum, should make energy companies more efficient through less time and less cost. Accenture believes the IT trends and innovations discussed here will provide energy companies with opportunities to reduce costs, improve competitiveness, increase focus on their core businesses, and ultimately, achieve higher performance.

Neale Johnson is senior director and the plant optimization lead for Accenture Plant and Automation Solutions. He has 18 years of downstream energy experience, including 13 years of consulting in refining. During this time, Johnson worked with many of the supermajors, developing strategies ranging from developing key performance indicators, to improving procurement, developing strategy, and detailing control systems.

Hemme Battjes is an analyst in Accenture’s energy industry group. He works on analyzing application portfolios and IT due diligence in the downstream energy segment.
For other great articles about exploration, drilling, completions and production, subscribe to The American Oil & Gas Reporter and bookmark www.aogr.com.